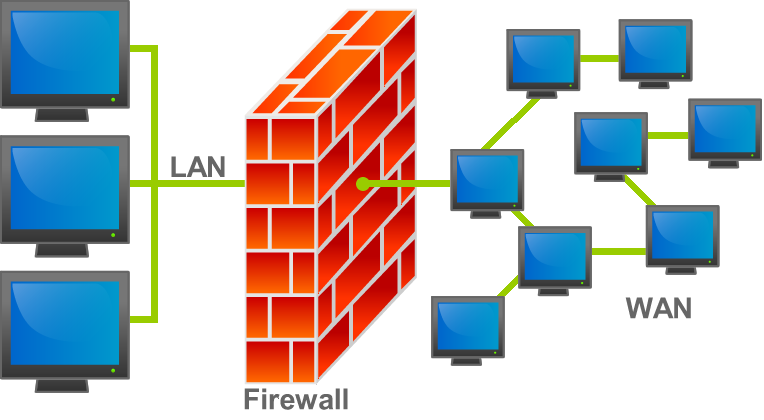
A firewall is a device used in network security to monitor incoming and outgoing network traffic. This determines whether to allow or block certain traffic based on a predefined set of security rules. While authorized traffic can reach its destination, unauthorized traffic can be prevented.
Its functionality has changed over the years, allowing the firewall to be implemented in a variety of ways. Firewalls are configured through software or hardware tools, which we will discuss in this article. However, let's first look at how they work.
Firewall
Firewall
What is a firewall?
Firewall goals
In addition to being one of the most essential infrastructures for you, firewalls can help isolate computers and servers from the Internet to ensure data security and privacy. As mentioned earlier, they not only control traffic through your server but also generate traffic in some cases. The overall goal is to reduce or eliminate unwanted network connections and free flow of legitimate connections. Having this type of protection can be very valuable.
For example, if we think of a (DoS) attack, the wrong traffic will flood your site and can potentially crash the targeted website's server. Properly configured firewalls are there to protect your environment from such situations. If supported, inspection techniques allow traffic flow patterns to be analyzed for anomalies leading to an ongoing attack.
How do firewalls work?
Packet Filtering
Packet filtering is a special way to implement a firewall to monitor network connectivity. Data packets are units that are packed together and travel along a specific network path. Packets are analyzed and compared against configuration rules or "access lists". It then specifies whether authorized access to your environment is allowed or denied.
Inspection
As previously mentioned, inspection techniques allow traffic flow patterns to be analyzed to determine when an attack occurs. The way this is done by the firewall is that it does not determine what site or application you are currently accessing. In this case, the firewall will determine the authorized data from the website or application versus any data from a hacker or unauthorized source. , tracks the "conversation list".
Proxy based firewall
Proxy-based firewalls take inspection one step further. This type of implementation prevents direct network connection between internet traffic and the server. A firewall acts as an intermediary between your server and end user requests. Complete data packets are checked based on the set rules.


